Introduction to Windows Memory Forensics
This section introduces Windows Memory Forensics, explaining the critical role of analyzing system memory (RAM) in cybersecurity investigations.
- Memory forensics involves examining a system’s physical memory to uncover evidence of cybercrimes or system failures.
- Memory dumps store valuable data lost during system reboots, such as running programs, user activity, and potential malware.
- It provides insights into system status and can help in uncovering malicious software.
- The course introduces tools like FTK Imager and Volatility3 for capturing and analyzing memory dumps.
- Effective analysis requires understanding Windows memory structures and the use of advanced forensics techniques.
Capturing Memory Dumps
This section focuses on the process of capturing memory dumps, an essential step for memory forensics.
- Memory dumps capture the entire contents of a system’s memory, which is crucial for post-incident analysis.
- Tools like AccessData FTK Imager and Volatility3 are used for both capturing and analyzing memory dumps.
- The process involves specifying paths and selecting memory areas, including the pagefile for a complete image.
- FTK Imager ensures data integrity by using hash functions like MD5 and SHA1.
- Memory dumps can reveal hidden malware, encryption keys, and network connections.
Analyzing the Memory Dump
This section covers how to analyze a memory dump to uncover critical evidence of user activity, running processes, and potential malware.
- Memory dump analysis involves examining processes, network connections, and user activity.
- Tools like Volatility3 help identify running processes and loaded DLLs.
- The command-line arguments used by running processes provide clues about malicious activity.
- Identifying malware through memory structures is a key aspect of forensics.
- Using Volatility’s plugins like windows.pslist and windows.netscan allows for a comprehensive review of system activity.
Hands-On Lab Environment – 1 :
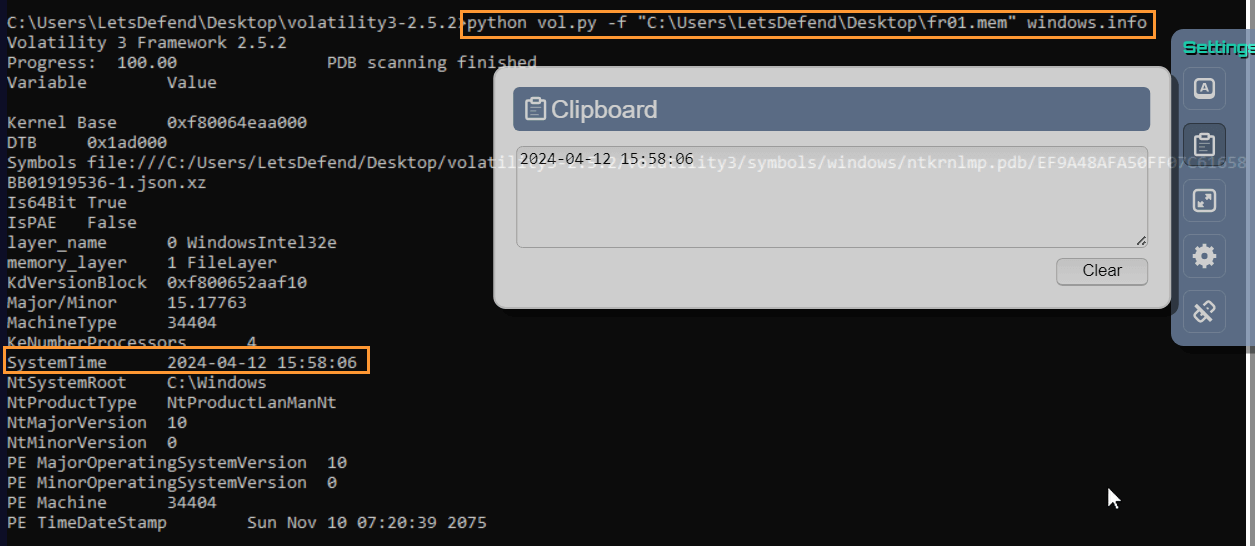
Question: What is the “System Time” according to the memory dump file “fr01.mem”?
Answer: 2024-04-12 15:58:06
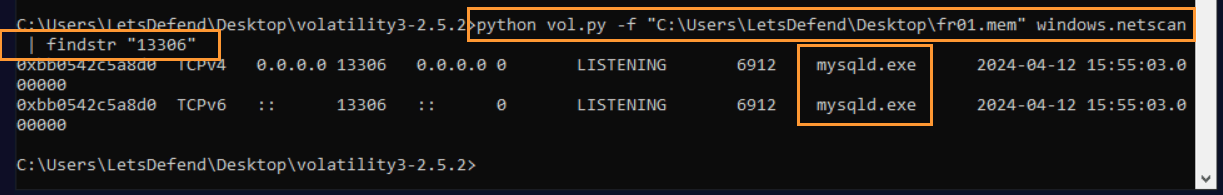
Question: What is the name of the process listening on “port 13306” according to the memory dump file “fr01.mem”?
Answer: mysqld.exe
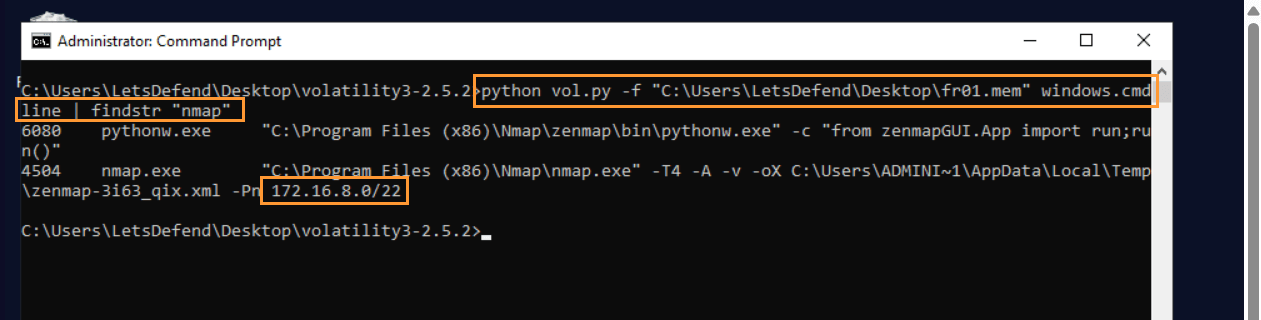
Question: When you examine the memory dump file “fr01.mem”, what tool is used for the “MITRE T1046 – Network Service Discovery” technique?
Answer: nmap.exe
Question: According to the “fr01.mem” memory dump file, what is the IP block targeted by the “port scan” activity?
Answer: 172.16.8.0/22
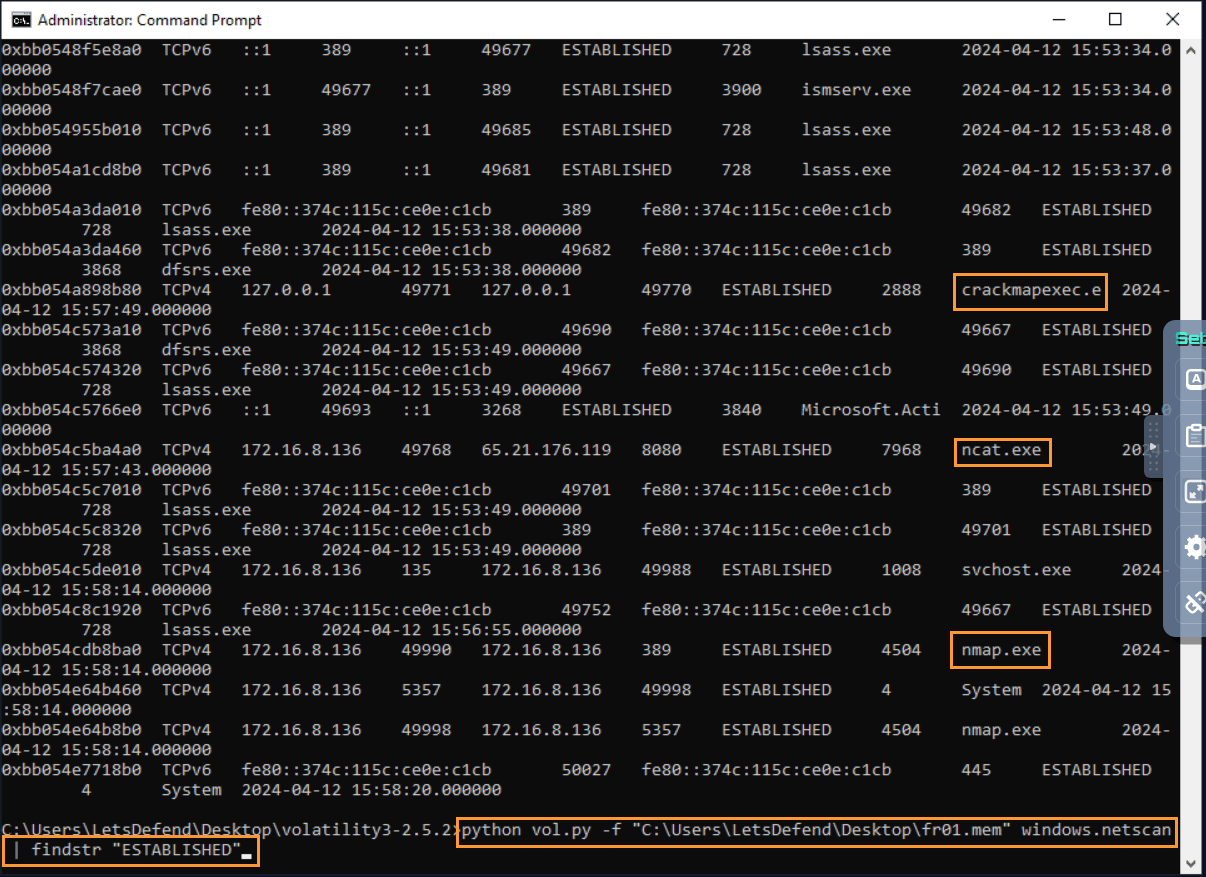
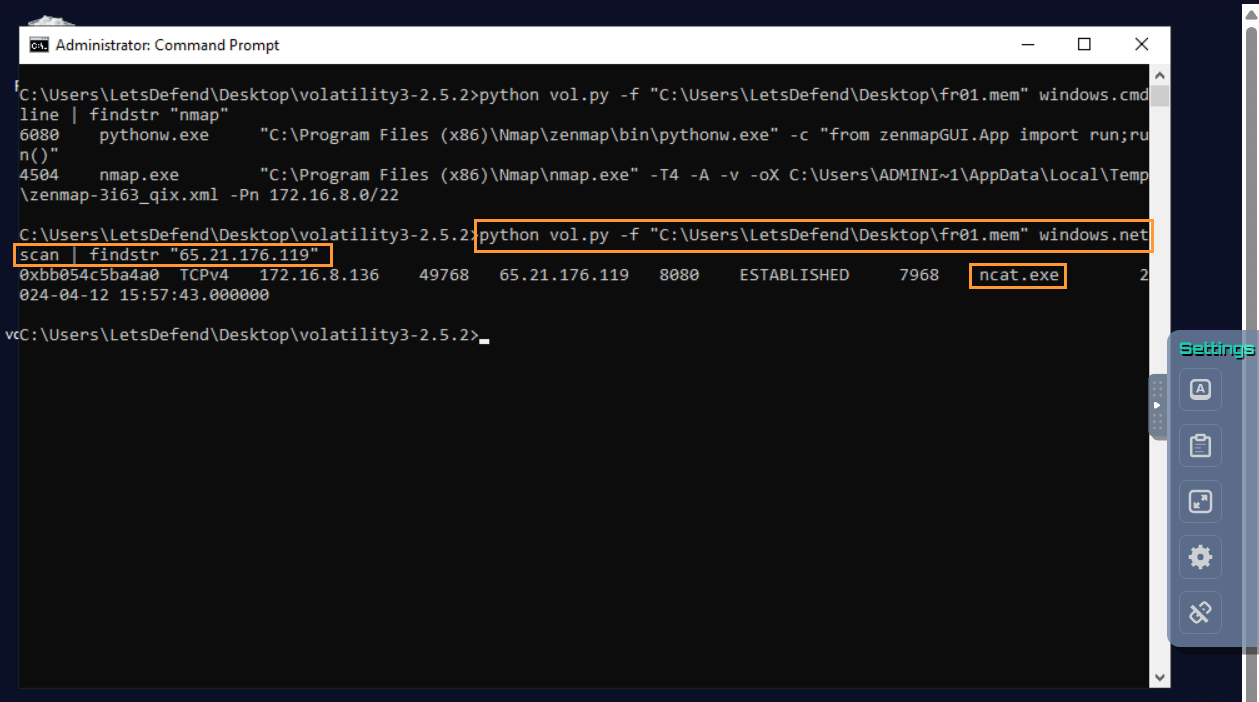
Question: According to the memory dump file “fr01.mem”, what is the name of the application communicating with the IP address “65.21.176.119”?
Answer: ncat.exe
Basic Memory Analysis
This section explains the basic methods and tools used for analyzing memory dumps, helping identify potential threats.
- Basic analysis begins with image identification, ensuring the dump file format is accurate for analysis.
- Processes and threads are listed to identify suspicious or hidden activities.
- Analyzing network connections and open ports reveals external threats or command-and-control (C2) communication.
- The Windows registry can provide insights into system configuration and user actions.
- Malware analysis is crucial, with tools like Volatility3’s yarascan helping detect hidden threats in memory.
Hands-On Lab Environment – 2 :
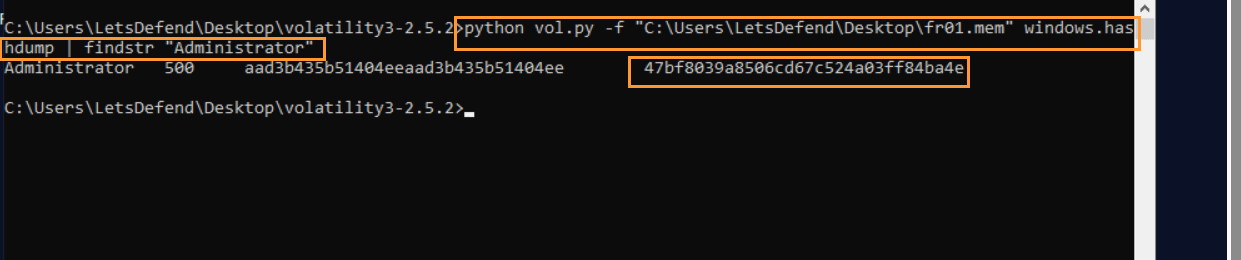
Question: Examine the “fr01.mem” memory dump file, what is the NT hash value of the “Administrator” user?
Answer: 47bf8039a8506cd67c524a03ff84ba4e
Command used: python vol.py -f "C:\Users\LetsDefend\Desktop\fr01.mem" windows.hashdump | findstr "Administrator"
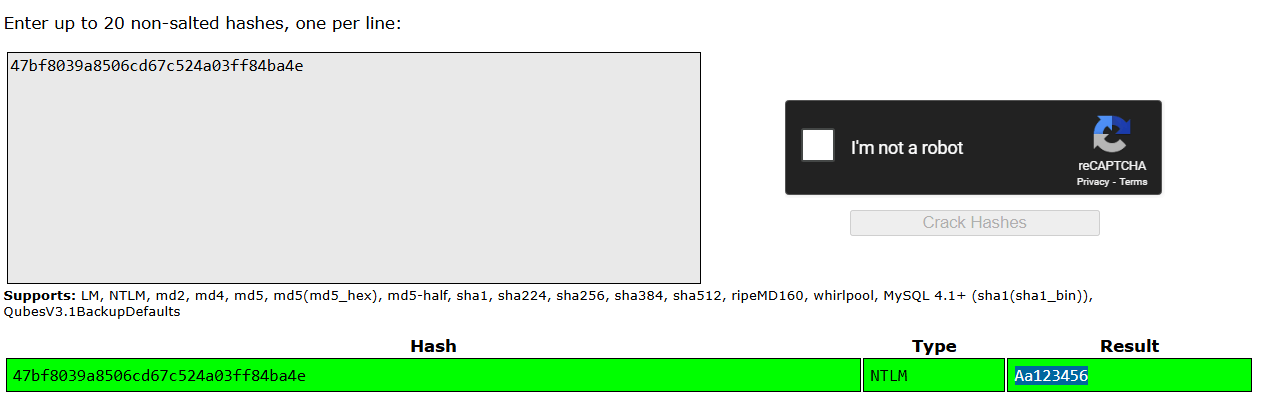
Question: Examine the memory dump file “fr01.mem”, what is the password for the “Administrator” user?
Answer: Aa123456
Web tool: Crackstation
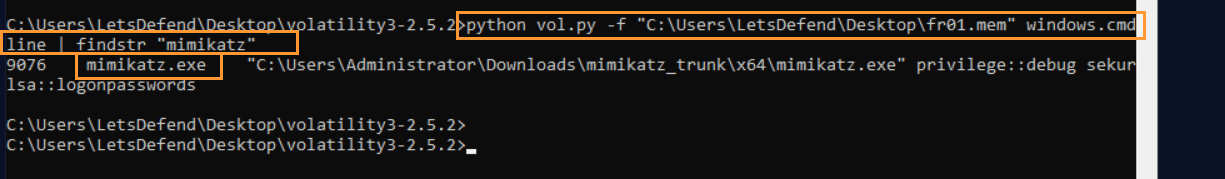
Question: Examine the “fr01.mem” memory dump file, what tool is used for the “MITRE T1003 – OS Credential Dumping” technique?
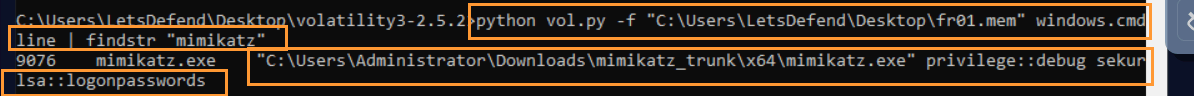
Answer: mimikatz.exe
Command used: python vol.py -f "C:\Users\LetsDefend\Desktop\fr01.mem" windows.cmdline | findstr "mimikatz"
Question: Examine the memory dump file “fr01.mem”. What were the parameters of the tool used for the “MITRE T1003 – OS Credential Dumping” technique?
Answer: "C:\Users\Administrator\Downloads\mimikatz_trunk\x64\mimikatz.exe" privilege::debug sekurlsa::logonpasswords
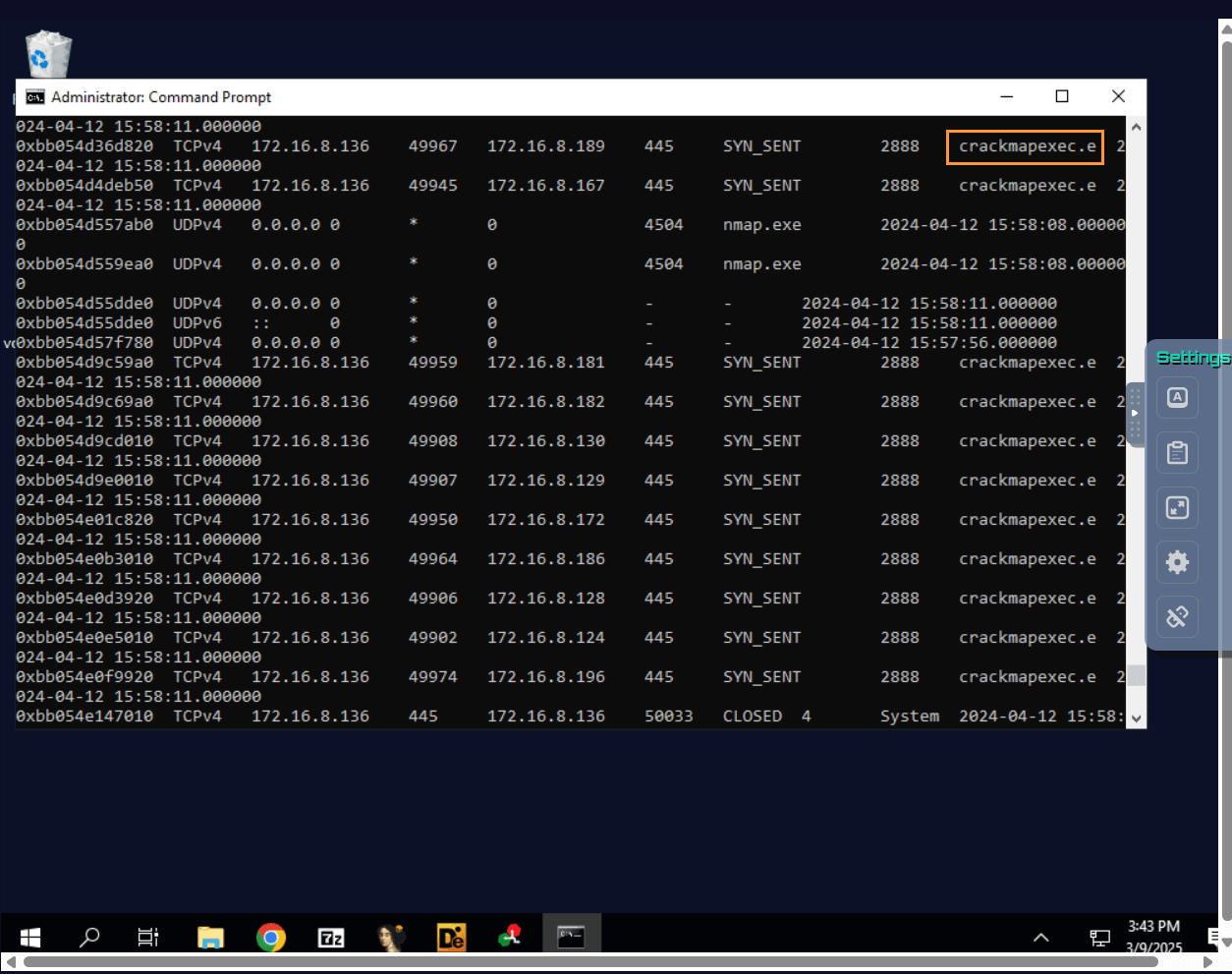
Question: Examine the “fr01.mem” memory dump file, which tool is used for the “MITRE T1550.002 – Use Alternate Authentication Material: Pass the Hash” technique?
Answer: crackmapexec
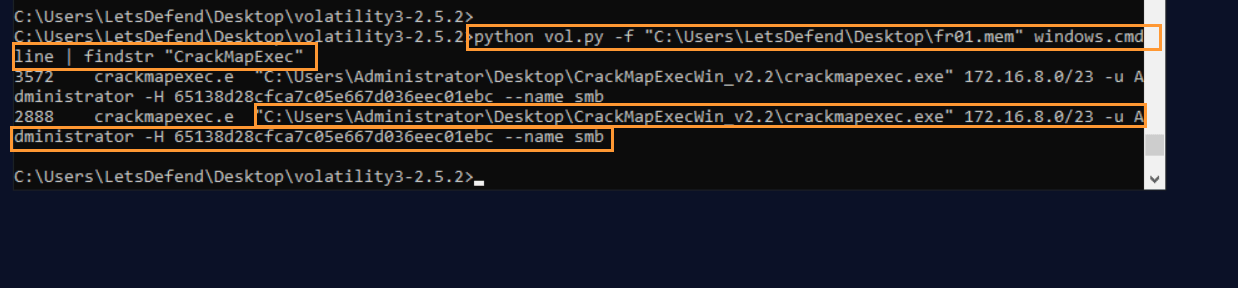
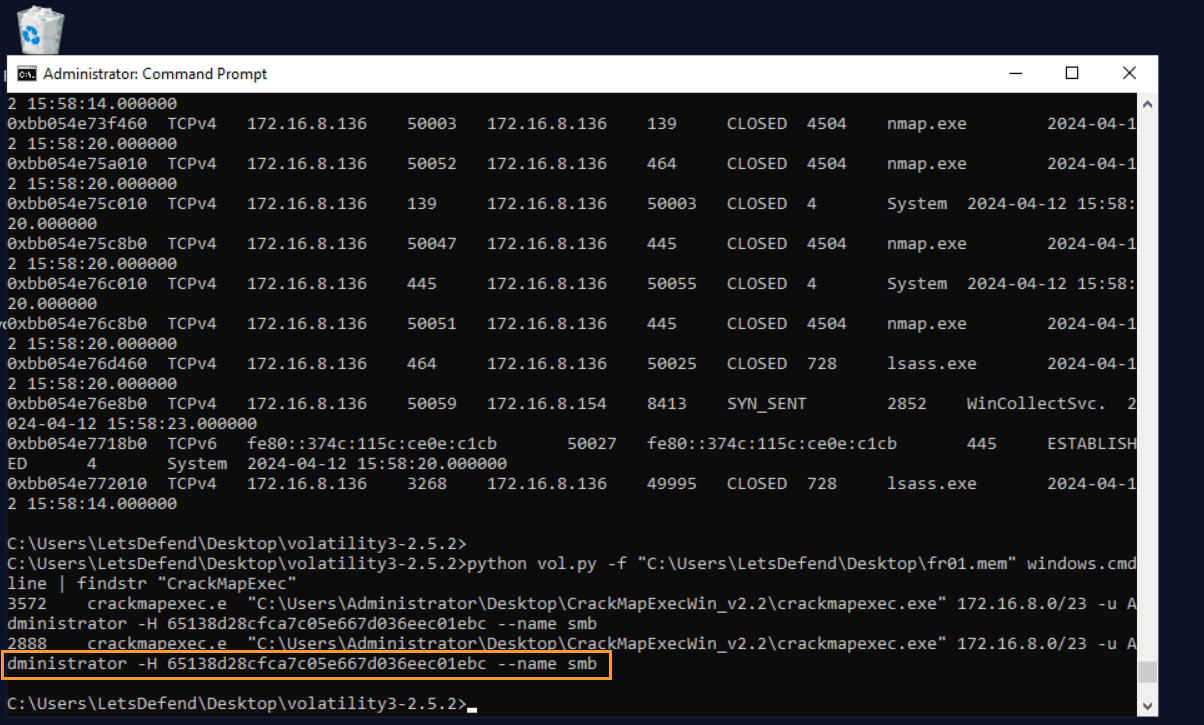
Question: Examine the memory dump file “fr01.mem”. What were the parameters of the tool used for the “MITRE T1550.002 – Use Alternate Authentication Material: Pass the Hash” technique?
Answer: "C:\Users\Administrator\Desktop\CrackMapExecWin_v2.2\crackmapexec.exe" 172.16.8.0/23 -u Administrator -H 65138d28cfca7c05e667d036eec01ebc --name smb
Question: Examine memory dump file “fr01.mem”, what hash value is used in the “MITRE T1550.002 – Use Alternate Authentication Material: Pass the Hash” activity?
Answer: 65138d28cfca7c05e667d036eec01ebc
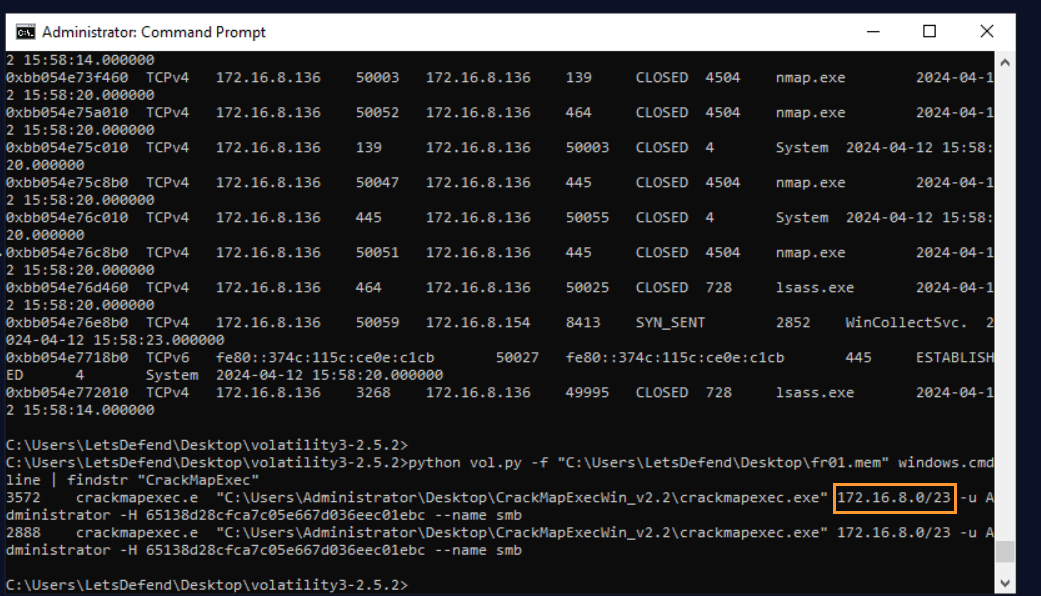
Question: Examine memory dump file “fr01.mem”, what IP block is targeted by the “MITRE T1550.002 – Use Alternate Authentication Material: Pass the Hash” technique?
Answer: 172.16.8.0/23
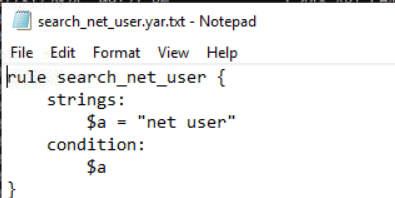
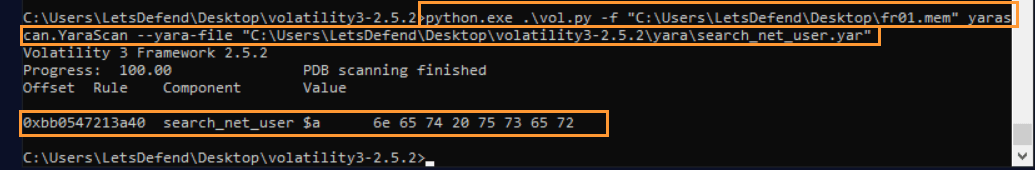
Question: What is the offset value when searching for the string expression “net user” in the memory dump file “fr01.mem”?
Answer: 0xbb0547213a40
Case Studies and Practical Examples
This section presents real-world examples of using Windows Memory Forensics to detect and analyze specific threats.
- Port Scan Detection: Identifies network scans through nmap.exe in memory dumps.
- Brute Force Attacks: Detects rapid login attempts using hydra and unusual network traffic.
- Credential Dumping: Mimikatz.exe is identified in memory, used to extract passwords from a system.
- These examples highlight how memory forensics tools like Volatility3 are essential for detecting attacks and gathering evidence in digital forensics.


Leave a Reply