The “SOC Fundamentals” course is a foundational step for anyone looking to build a rewarding career in cybersecurity as a Security Operations Center (SOC) analyst. This comprehensive course covers essential topics, from the structure and operations of a SOC to the tools and responsibilities of an analyst. Here’s an overview of what I learned and accomplished in each section of this course, along with the skills I developed.
SOC Fundamentals Overview
The course began with an introduction to the purpose and structure of a SOC. It emphasized the critical role SOC analysts play in detecting, analyzing, and responding to cybersecurity incidents. The importance of understanding tools like SIEM, EDR, and SOAR was highlighted, as well as the need to adopt a proactive mindset.
Key Takeaways:
- Importance of SOC tools such as Log Management, SIEM, and EDR.
- Common mistakes made by SOC analysts and how to avoid them.
- Developing a strategic approach to cybersecurity challenges.

Introduction to SOC
In this section, I learned about the fundamental operations and tools within a SOC. It detailed how SOC tools work and why they are essential for analysts.
Key Takeaways:
- Structure and operation of a SOC.
- Overview of SOC tools and their usage.
- The role of a SOC analyst in mitigating cybersecurity risks.

SOC Types and Roles
This section delved into the various SOC models, including In-house, Virtual, Co-managed, and Command SOCs. The relationship between people, processes, and technology within a SOC was also explored.
Key Takeaways:
- Different SOC models and their use cases.
- The “People, Process, and Technology” framework for a successful SOC.
- Roles within a SOC: SOC Analyst, Incident Responder, Threat Hunter, Security Engineer, and SOC Manager.

SOC Analyst and Their Responsibilities
Here, I gained a deeper understanding of the SOC analyst’s role. I explored the daily activities of an analyst, such as reviewing alerts and utilizing tools like SIEM and EDR.
Key Takeaways:
- Key skills for SOC analysts: operating system knowledge, networking fundamentals, and malware analysis.
- Responsibilities include initial threat investigation and escalation when necessary.
- Tools and techniques to analyze SIEM alerts effectively.

SIEM and Analyst Relationship
This section focused on the relationship between SOC analysts and SIEM solutions. I learned how SIEM works and how it supports analysts by collecting and filtering data to generate alerts.
Key Takeaways:
- Functions of SIEM in real-time event logging and threat detection.
- Understanding false positives and optimizing alerting processes.
- Tools like Splunk, IBM QRadar, and ArcSight ESM.

Log Management
Log management was introduced as a critical component of a SOC. This section emphasized its importance in efficiently managing logs from multiple sources and investigating security incidents.
Key Takeaways:
- Centralized log management for time efficiency and accuracy.
- How to investigate malware communications using log management.
- Real-world examples of analyzing suspicious IPs or malware.

EDR – Endpoint Detection and Response
This section explored EDR solutions, which are integral to monitoring and analyzing endpoint devices. The live investigation and containment features were particularly insightful.
Key Takeaways:
- EDR as a real-time monitoring and response tool.
- How to perform live investigations and isolate compromised devices.
- Common EDR tools: CarbonBlack, SentinelOne, and FireEye HX.
SOAR (Security Orchestration Automation and Response)
The role of SOAR solutions in streamlining SOC operations was explored in this section. It highlighted automation and centralization as key benefits.
Key Takeaways:
- Automating tasks such as IP reputation checks and sandbox analysis.
- Using playbooks to standardize and streamline alert investigations.
- Integrating multiple security tools for cohesive analysis.
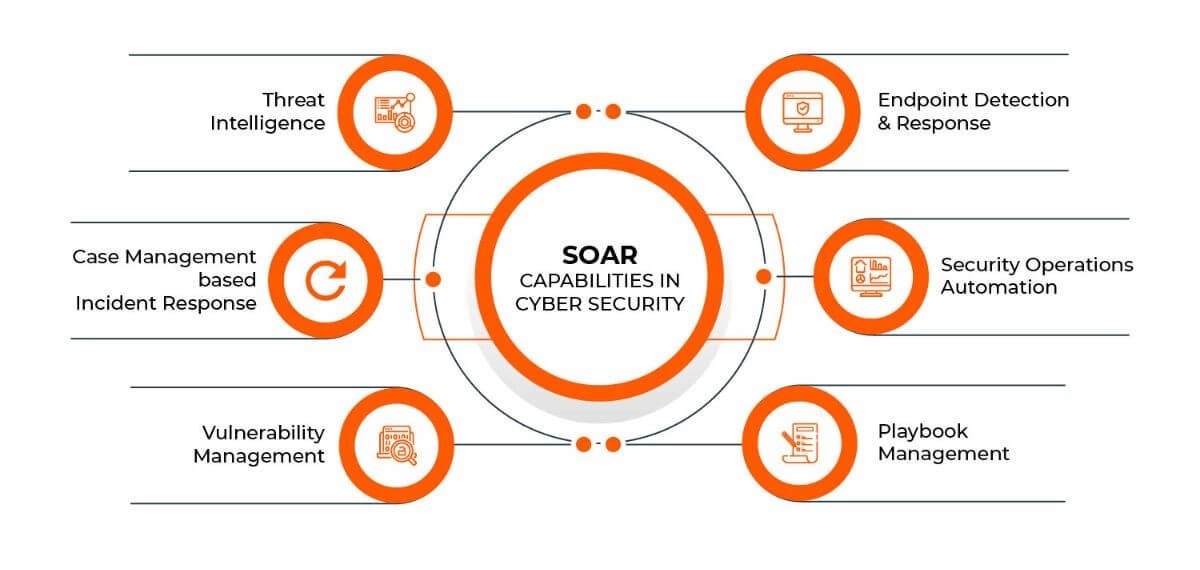
Threat Intelligence Feed
Threat intelligence feeds were presented as vital resources for SOC analysts. They provide data on known threats and help analysts investigate potential incidents.
Key Takeaways:
- Using threat intelligence feeds like VirusTotal and Talos Intelligence.
- Understanding the limitations of feeds and ensuring comprehensive analysis.
- Importance of verifying threat data and maintaining skepticism.
Common Mistakes Made by SOC Analysts
This section identified frequent errors and provided guidance on avoiding them. Examples included over-reliance on tools like VirusTotal and inadequate log analysis.
Key Takeaways:
- Importance of thorough analysis and avoiding over-reliance on automated tools.
- Understanding the nuances of threat intelligence and sandbox environments.
- How to use logs effectively to uncover hidden threats.

Skills Gained
- Comprehensive understanding of SOC operations and tools.
- Proficiency in SIEM, Log Management, EDR, and SOAR solutions.
- Practical skills in threat intelligence and malware analysis.
- Ability to identify and avoid common SOC analyst mistakes.
- Strong foundational knowledge for advancing in cybersecurity roles.

The “SOC Fundamentals” course provided me with a robust foundation for a career as a SOC analyst. Each section contributed valuable insights and hands-on experience, preparing me for the dynamic challenges of cybersecurity. I look forward to applying these skills in real-world scenarios and continuing my learning journey.


Leave a Reply