Project Type: Windows Server | pfSense Firewall | Hybrid Lab Networking
Skill Level: Beginner–Intermediate
Lab Platform: Hyper-V + VMware + pfSense
Why I Built This
After building the core domain (wired.com) in Day 1, it was time to add real-world network segmentation and control to the lab. In Day 2, I installed pfSense as a virtual firewall, connected both my Hyper-V and VMware environments to it, and properly segmented the network to prepare for future cloud integrations.
This mirrors real enterprise setups where firewalls tightly control traffic between different sites, clouds, and endpoints.
Lab Setup Overview
| Component | Details |
|---|---|
| Hypervisor 1 | Hyper-V (Main hypervisor) |
| Hypervisor 2 | VMware Workstation Pro |
| Firewall VM | pfSense 2.7.2 |
| WAN Switch | External_internet_switch (bridged to Wi-Fi NIC) |
| LAN Switch | Internal_Switch (private internal lab network) |
| VMware Custom Switch | VMnet19 (Bridged to Hyper-V Internal_Switch NIC) |
| Domain Name | wired.com |
| Subnet | 192.168.1.0/24 |
| pfSense LAN IP | 192.168.1.1 |
| DC1 (NYC-DC1-S22) IP | 192.168.1.10 |
| Client 1 (NYC-CLI1-W10) IP | 192.168.1.20 (DHCP Static) |
| DC2 (FL-DC1-S22) IP | 192.168.1.30 (Static) |
Step-by-Step Breakdown
Step 1: Created the Hyper-V Virtual Switches
- External_internet_switch: Created an “External” switch bound to my real Wi-Fi adapter.
- Internal_Switch: Created an “Internal” switch for isolated lab traffic between VMs.
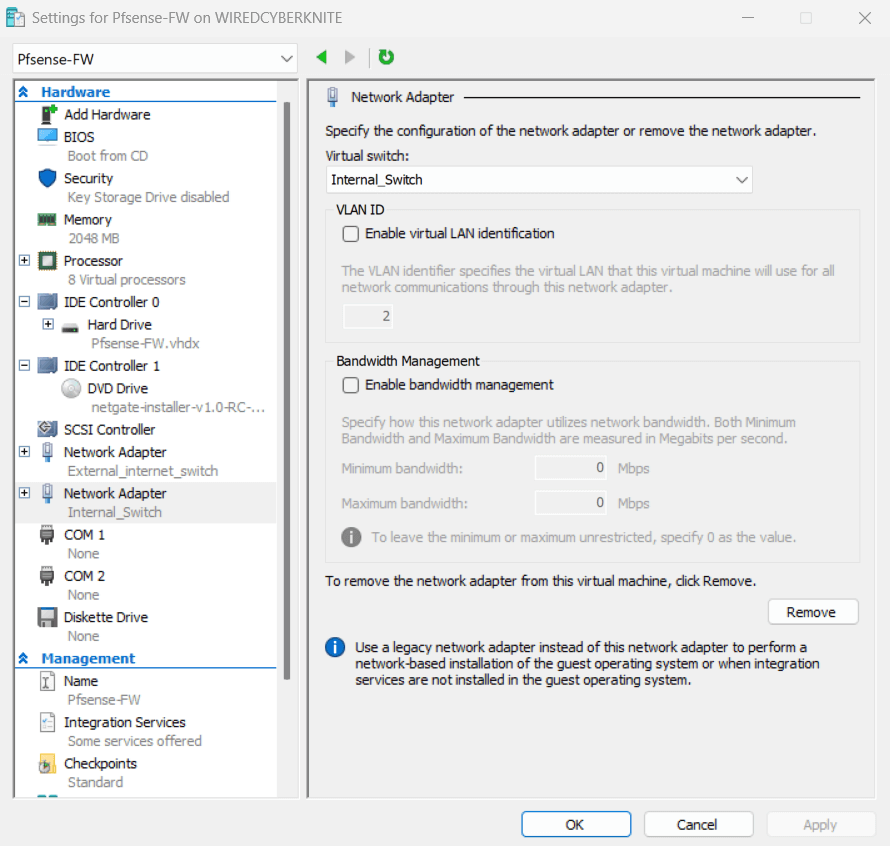
Step 2: Installed pfSense VM
- Created a pfSense VM with two NICs:
- WAN NIC: Connected to
External_internet_switch(Internet access) - LAN NIC: Connected to
Internal_Switch(isolated lab network)
- WAN NIC: Connected to
- Set the pfSense LAN static IP to 192.168.1.1/24
- Enabled DHCP on pfSense for the LAN network (192.168.1.100-192.168.1.200)
Step 3: Connected Hyper-V VMs to Internal_Switch
- NYC-DC1-S22 (Domain Controller) NIC switched to
Internal_Switch - NYC-CLI1-W10 (Client) NIC switched to
Internal_Switch - Both now route through pfSense for DNS and gateway.
Step 4: Configured VMware Connection
- Created VMnet19 as a Custom Bridged connection.
- Bridged VMnet19 directly to the “vEthernet (Internal_Switch)” Hyper-V adapter.
- Connected FL-DC1-S22 (Florida DC) NIC to VMnet19.
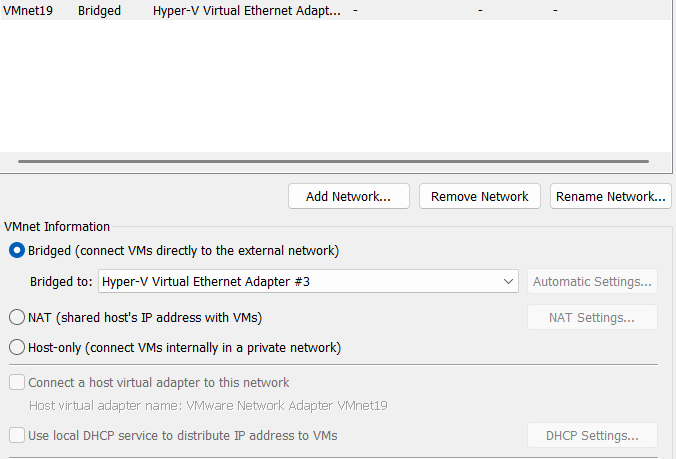
Now VMware and Hyper-V shared the same 192.168.1.0/24 network through pfSense!
Step 5: Set Static IPs
| Machine | IP Address | Subnet Mask | Gateway | DNS Server |
| NYC-DC1-S22 | 192.168.1.10 | 255.255.255.0 | 192.168.1.1 | 127.0.0.1 (itself) |
| NYC-CLI1-W10 | 192.168.1.20 | 255.255.255.0 | 192.168.1.1 | 192.168.1.10 |
| FL-DC1-S22 | 192.168.1.30 | 255.255.255.0 | 192.168.1.1 | 192.168.1.10 |
Step 6: Testing
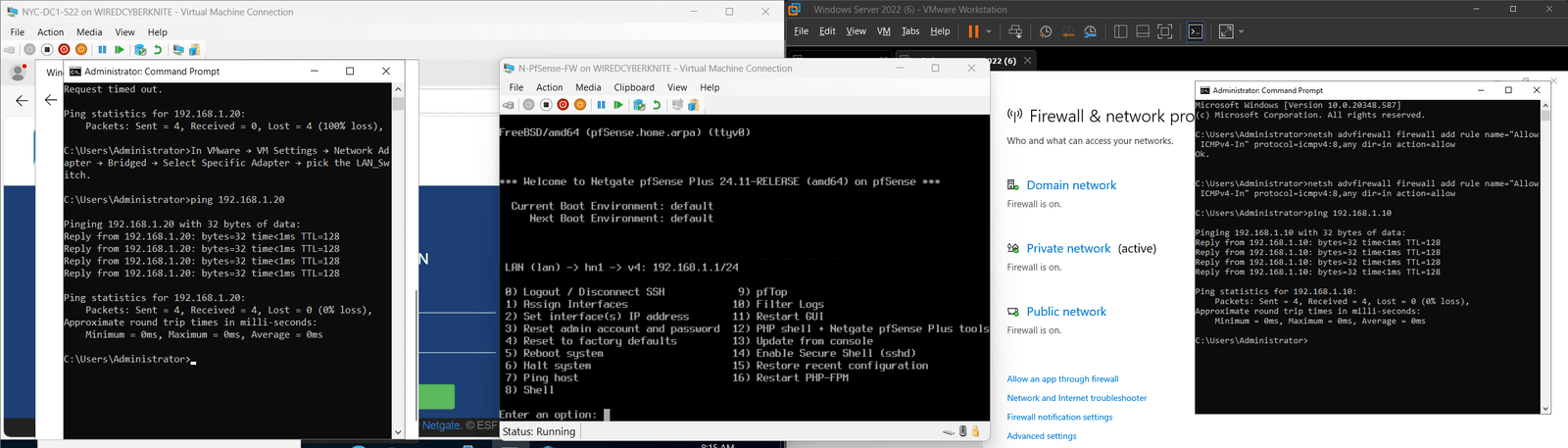
- Successfully pinged between:
- NYC-DC1-S22 ⇄ NYC-CLI1-W10
- NYC-DC1-S22 ⇄ FL-DC1-S22
- FL-DC1-S22 ⇄ NYC-CLI1-W10
- Verified all VMs could access pfSense GUI at https://192.168.1.1
- Verified internet access from CLI and FL-DC1 (filtered by pfSense)
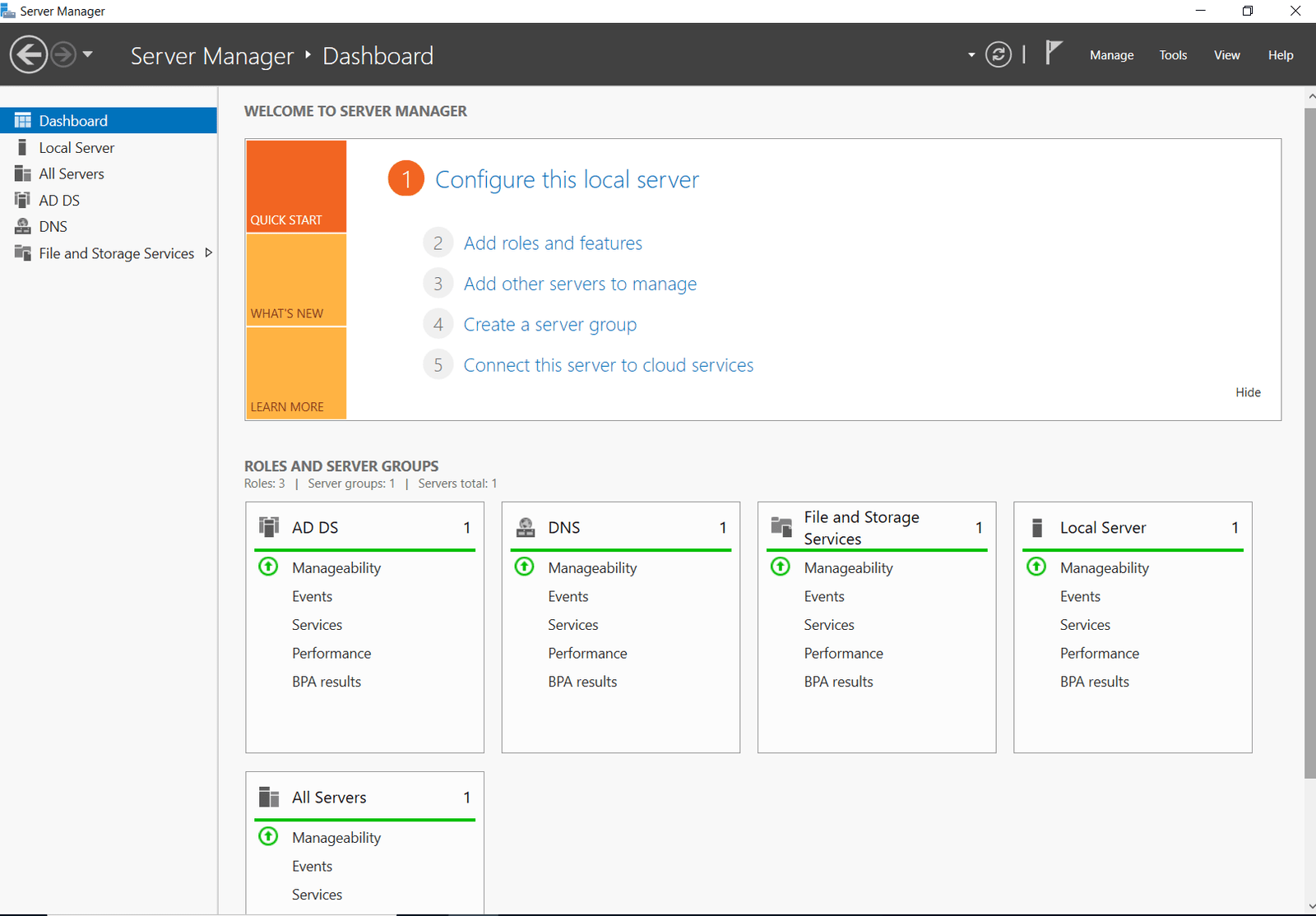
Step 6: Installed AD DS on FL-DC1-S22
- Installed Active Directory Domain Services (AD DS) role on FL-DC1-S22.
- Selected Add a domain controller to an existing domain.
- Joined FL-DC1-S22 to the existing wired.com domain.
- Ensured it became a full domain controller and Global Catalog (GC) without enabling Read-Only Domain Controller (RODC).
- Confirmed replication between NYC-DC1 and FL-DC1 was working.
Key Problems Solved
- Bridging Different Hypervisors: Instead of fighting with NAT/host-only weirdness, bridging through Hyper-V’s Internal_Switch made VMware and Hyper-V talk cleanly.
- IP Address Planning: Proper IP assignments kept the firewall gateway (pfSense) central without collisions.
- Traffic Isolation: Hyper-V and VMware were isolated behind pfSense but still had Internet access as needed.
- Multi-Site Domain Controller Setup: Successfully added a second DC (FL) to simulate a real-world multi-site domain.
Troubleshooting Tips
- Can’t Ping Between VMs?
- Check Windows Firewall. Allow ICMPv4 Echo Requests (Inbound).
- Can’t Reach pfSense GUI?
- Double-check you’re on the LAN interface (192.168.1.x subnet).
- VMware Not Bridging?
- Ensure VMnet19 is properly bridged to the Hyper-V Internal_Switch.
- FL DC Can’t Join Domain?
- Make sure DNS is pointing to NYC-DC1-S22 (192.168.1.10).
What I Learned
- How to deploy a fully functional firewall in a virtual lab.
- How to properly bridge two different hypervisors (Hyper-V and VMware) into one seamless network.
- How crucial it is to control IP space, DHCP, and gateways right from the start.
- How to install a second domain controller at a simulated remote site.
What’s Next?
In Day 3, I’ll:
- Build out Organizational Units (OUs)
- Bulk-create users with PowerShell
- Deploy Group Policies to simulate real-world IT environments
- Fine-tune domain replication settings between NYC and FL.
Stay tuned — the hybrid network is now fully alive!
Follow me on LinkedIn for new blog updates and behind-the-scenes!

Leave a Reply