The Cyber Kill Chain is a widely recognized framework designed by Lockheed Martin in 2011 to break down the stages of a cyber attack. This model provides cybersecurity professionals with insights into how attackers operate, allowing them to identify, prevent, and mitigate threats more effectively. Through this course, I gained an in-depth understanding of each phase of the Cyber Kill Chain and its significance in cybersecurity operations.

Introduction to the Cyber Kill Chain
The Cyber Kill Chain is a structured approach to understanding cyber attacks. Lockheed Martin developed this model to outline the steps attackers take, from initial reconnaissance to achieving their objectives. For Security Operations Center (SOC) analysts and cybersecurity professionals, mastering the Cyber Kill Chain helps in detecting, analyzing, and mitigating cyber threats.

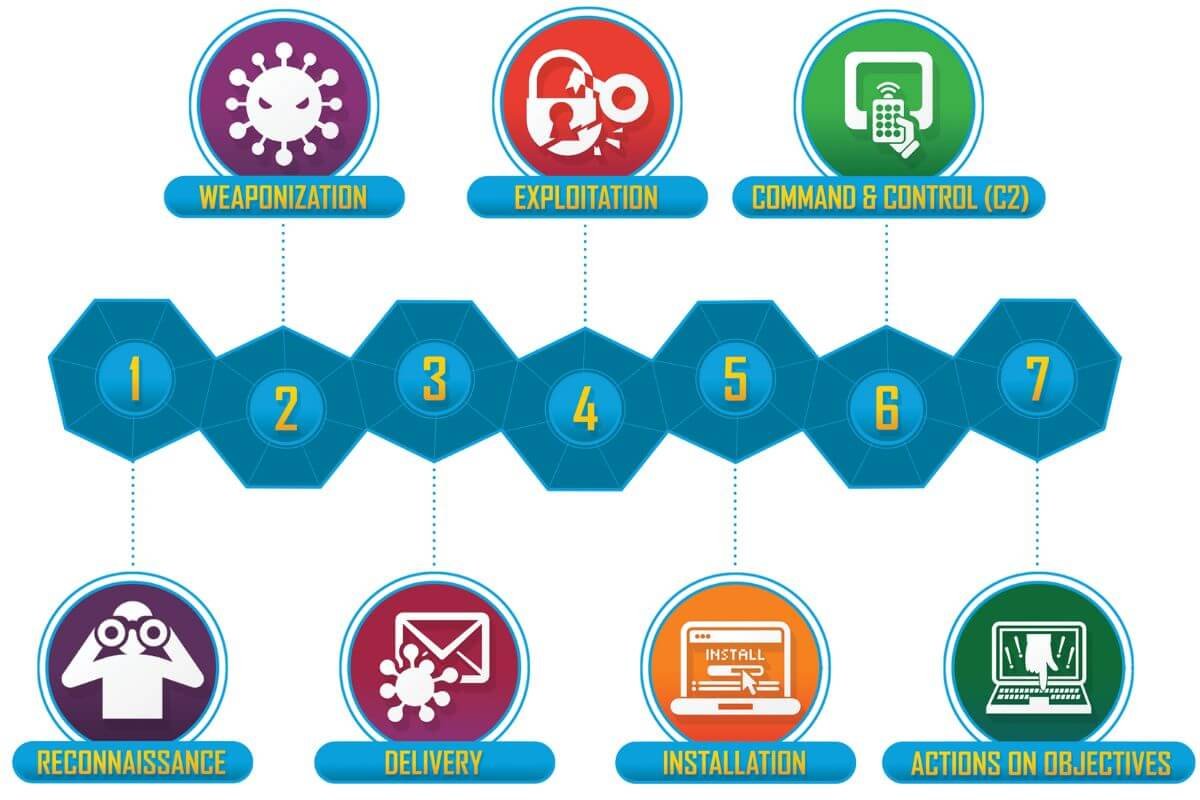
Cyber Kill Chain Steps
The framework consists of seven sequential stages, where attackers must successfully complete each step before progressing to the next. If defenders disrupt the attack at any phase, the entire chain can be broken.
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (C2)
- Actions on Objectives
Each of these steps represents a critical point in an attack that defenders can monitor and counteract.
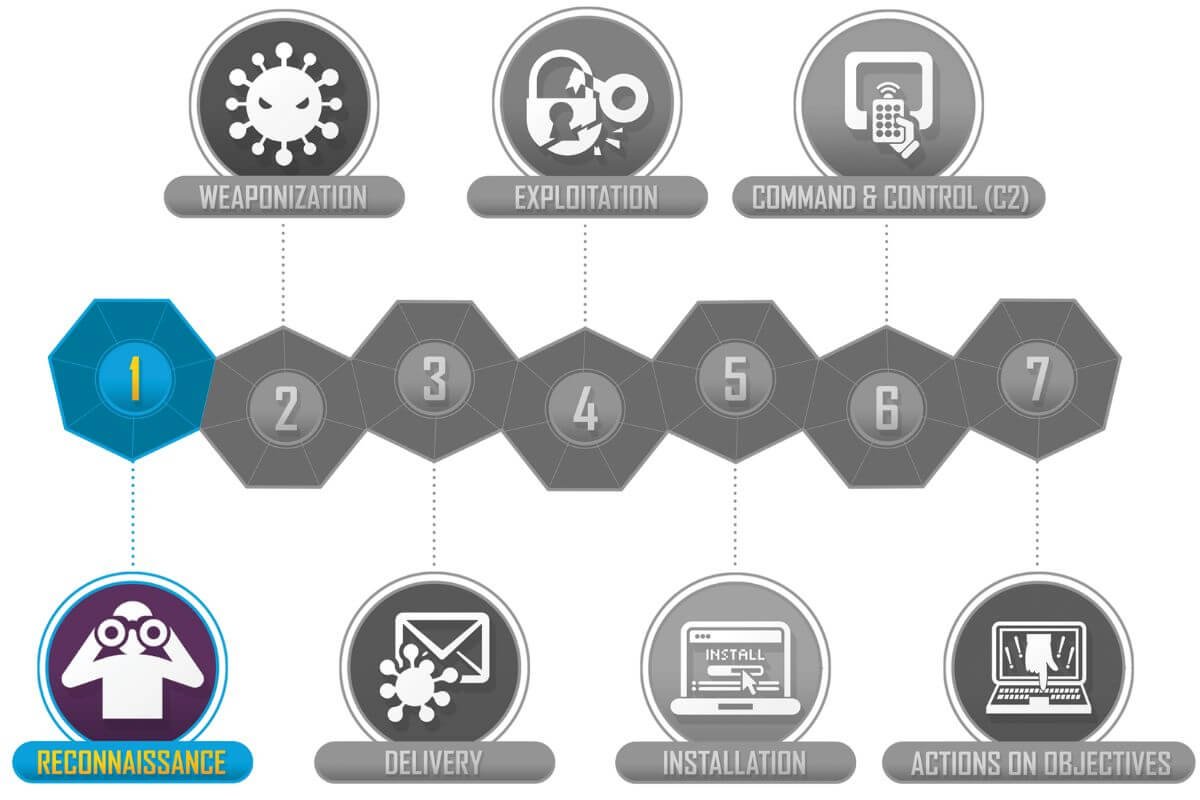
1. Reconnaissance
The first step involves the attacker gathering information about the target. This phase is crucial as it determines the attack vector.
- Adversary Tactics: Collecting open-source intelligence (OSINT), scanning for vulnerabilities, and gathering employee email addresses.
- Defender Strategies: Organizations can minimize exposure by conducting external security assessments, monitoring for information leaks, and limiting publicly available sensitive data.
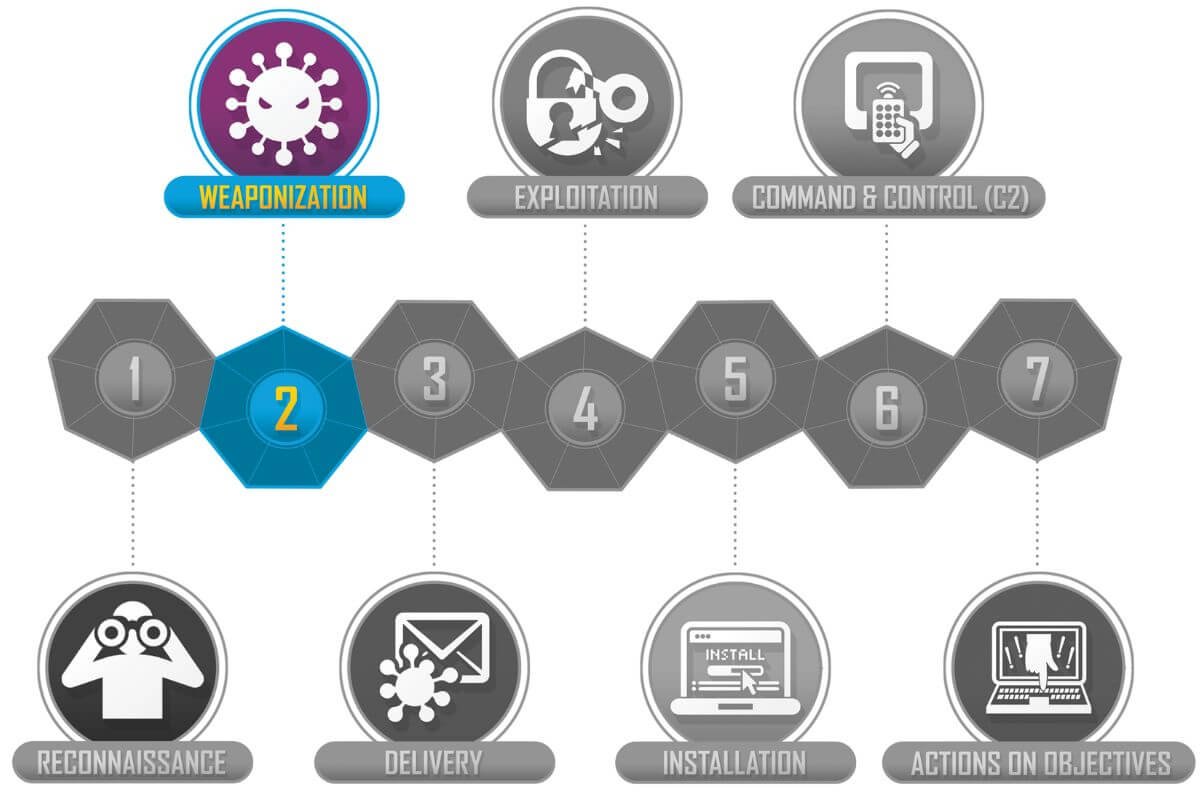
2. Weaponization
At this stage, attackers develop or acquire tools necessary for the attack, such as malware or exploit kits.
- Adversary Tactics: Creating malicious software, designing phishing campaigns, and embedding exploits in documents.
- Defender Strategies: Regular vulnerability assessments, patch management, and monitoring emerging cyber threats can help prevent weaponization.
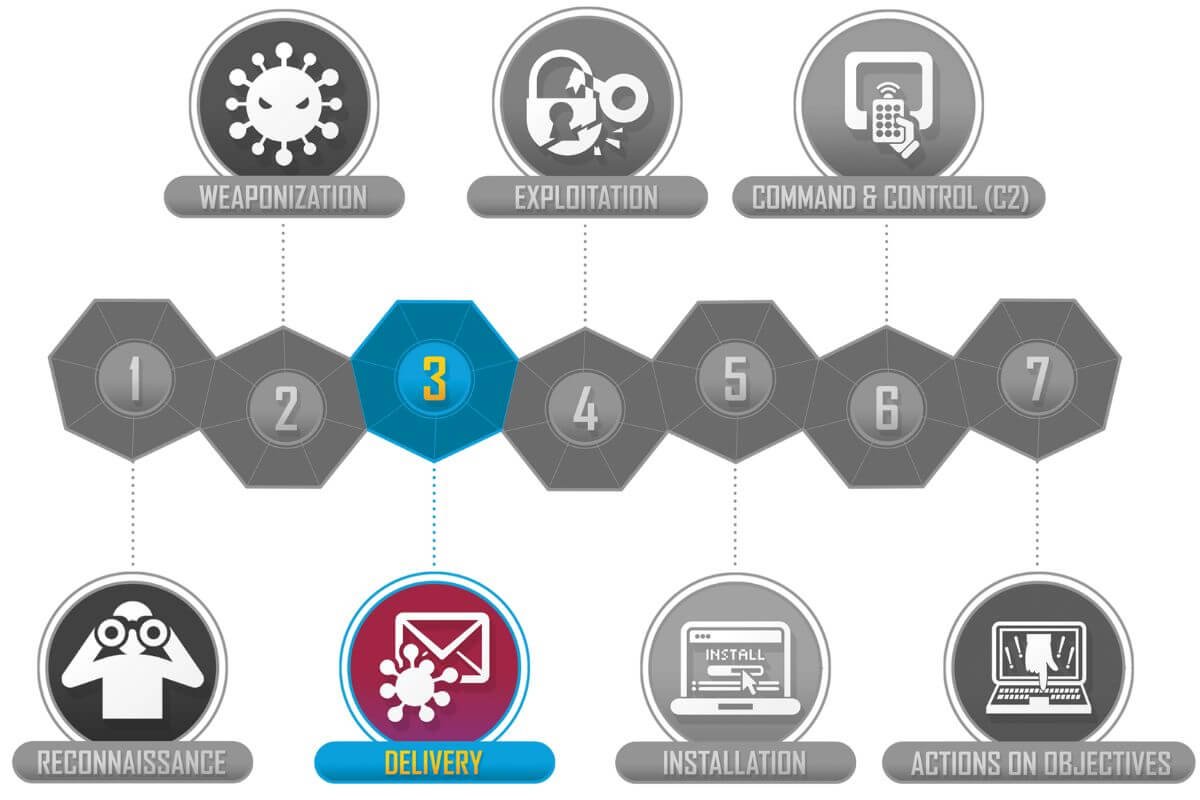
3. Delivery
This phase involves delivering the malicious payload to the victim via email, USB, drive-by downloads, or other methods.
- Adversary Tactics: Sending phishing emails, hosting malicious files, and exploiting software vulnerabilities.
- Defender Strategies: Email security solutions, user awareness training, and behavior-based threat detection can reduce the likelihood of successful delivery.
4. Exploitation
Once the payload is delivered, attackers exploit system vulnerabilities to gain access.
- Adversary Tactics: Executing malicious scripts, leveraging unpatched vulnerabilities, and exploiting social engineering tactics.
- Defender Strategies: Endpoint Detection and Response (EDR), system hardening, and security patching can limit exploitation risks.
5. Installation
At this point, attackers install malware or backdoors to maintain persistent access to the system.
- Adversary Tactics: Deploying trojans, keyloggers, rootkits, or remote access tools.
- Defender Strategies: Network monitoring, anomaly detection, and threat hunting can help identify and remove unauthorized installations.
6. Command and Control (C2)
The attacker establishes a communication channel with the compromised system to control it remotely.
- Adversary Tactics: Connecting to C2 servers, using encrypted channels, and obfuscating traffic.
- Defender Strategies: Blocking known malicious IP addresses, monitoring network traffic for anomalies, and deploying intrusion detection systems (IDS).
7. Actions on Objectives
The final phase where the attacker executes their intended goals, such as data exfiltration, destruction, or further lateral movement within the network.
- Adversary Tactics: Encrypting files (ransomware), stealing sensitive data, and creating backdoors for future attacks.
- Defender Strategies: Implementing Data Loss Prevention (DLP), restricting access controls, and continuous security monitoring.
Key Takeaways from the Cyber Kill Chain Course
- Understanding how attackers progress through each phase enhances threat detection and response.
- Security teams should focus on breaking the attack chain at its earliest stages to prevent escalation.
- Continuous monitoring, security awareness training, and proactive defense strategies are essential in mitigating cyber threats.
By mastering the Cyber Kill Chain, I have gained a deeper understanding of cyber attack methodologies and how to effectively combat them. This knowledge is invaluable for SOC analysts and cybersecurity professionals in protecting organizations from advanced threats
If you want to learn more, check out the Let’sDefend website or take the course at this website: https://app.letsdefend.io/path/soc-analyst-learning-path.


Leave a Reply