LetsDefend
-
Windows Memory Forensics | Letsdefend
Introduction to Windows Memory Forensics This section introduces Windows Memory Forensics, explaining the critical role of analyzing system…
-
Network Packet Analysis | letsdefend
Introduction to Network Packet Analysis This section introduces the core concepts of network packet analysis, emphasizing its importance…
-
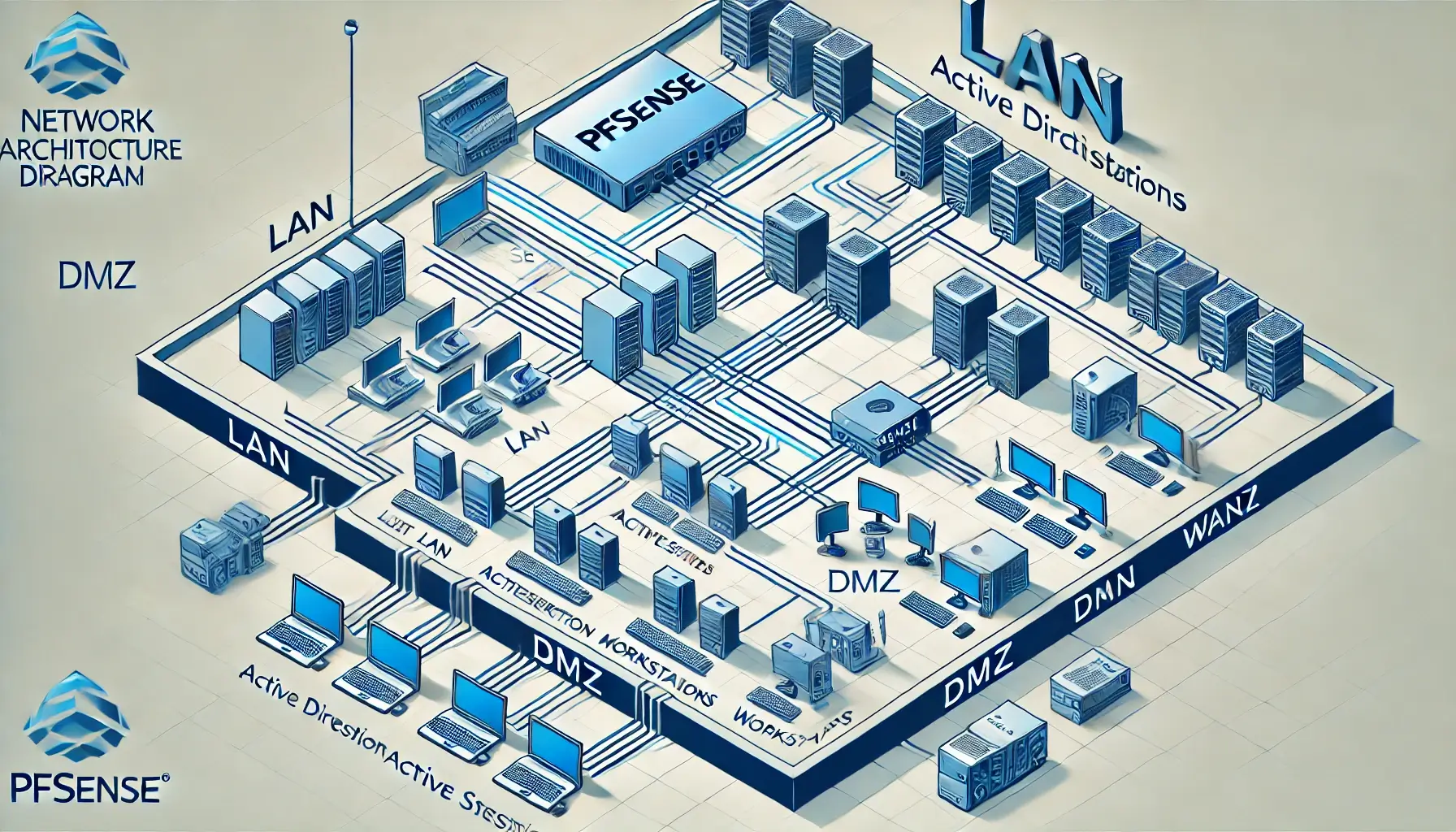
Secure Network Design | letsdefend
Introduction to Secure Network Design This section introduces the importance of secure network infrastructure and provides an overview…
-
Linux Memory Forensics | letsdefend
Introduction to Linux Memory Forensics This section introduces the importance and purpose of memory forensics in Linux systems.…
-
Network Design and Security Products | Letsdefend
Introduction to Network Design This section highlights the importance of network design as a fundamental aspect of creating…
-
Achieving Mastery: My Journey Through the SOC Analyst Learning Path with Let’sDefend
As cybersecurity threats continue to evolve, the role of the Security Operations Center (SOC) analyst becomes increasingly critical.…
-
Building a SOC Lab at Home: A Detailed Overview
In this blog, I’ll provide an overview of how I built a SOC (Security Operations Center) lab at…
-
Step-by-Step Malware Analysis Answer Lab Walkthrough | LetsDefend
Introduction This guide will help you run through a malware analysis environment, including both static and dynamic analysis…
-
Building a Malware Analysis Lab | Flare-VM | Windows 10 | LetsDefend
Introduction As an analyst or incident responder, there are times during investigations when you need a malware analysis…
-
SOC138 – Detected Suspicious XLS File Walkthrough | LetsDefend | Event ID: 77
In this walkthrough, I will guide you through the process of investigating a suspicious XLS file. Each step…