Project Type: Windows Server | Active Directory | Hybrid Lab Foundation
Skill Level: Beginner–Intermediate
Lab Platform: Hyper-V (preparing for VMware + pfSense + Cloud)
Why I Built This
This is the foundational step in my 10-Day hands-on IT lab series, where I’m preparing a hybrid virtualization environment using Hyper-V, VMware, and pfSense — eventually connecting it all to the cloud.
In Day 1, I focused on deploying Active Directory Domain Services (AD DS) in a clean Windows Server 2022 environment. This domain will be the core of my lab where I’ll later manage policies, control identity, route traffic securely, and simulate multi-site and cloud-connected infrastructure.
Lab Setup Overview
| Component | Details |
|---|---|
| Hypervisor | Hyper-V (on my main system) |
| DC VM Name | NYC-DC1-S22 (Windows Server 2022) |
| Client VM Name | NYC-CLI1-W10 (Windows 10) |
| Domain Name | wired.com |
| Subnet | 192.168.1.0/24 |
| DC IP Address | 192.168.1.10 (Static) |
| DNS Server | 127.0.0.1 (the DC itself) |
| Client DNS | Points to DC (192.168.1.10) |
Step-by-Step Breakdown
Step 1: Created the Domain Controller (NYC-DC1-S22)
I already had ISOs for both Windows Server 2022 and Windows 10 from earlier projects. So I spun up two VMs in Hyper-V right away:
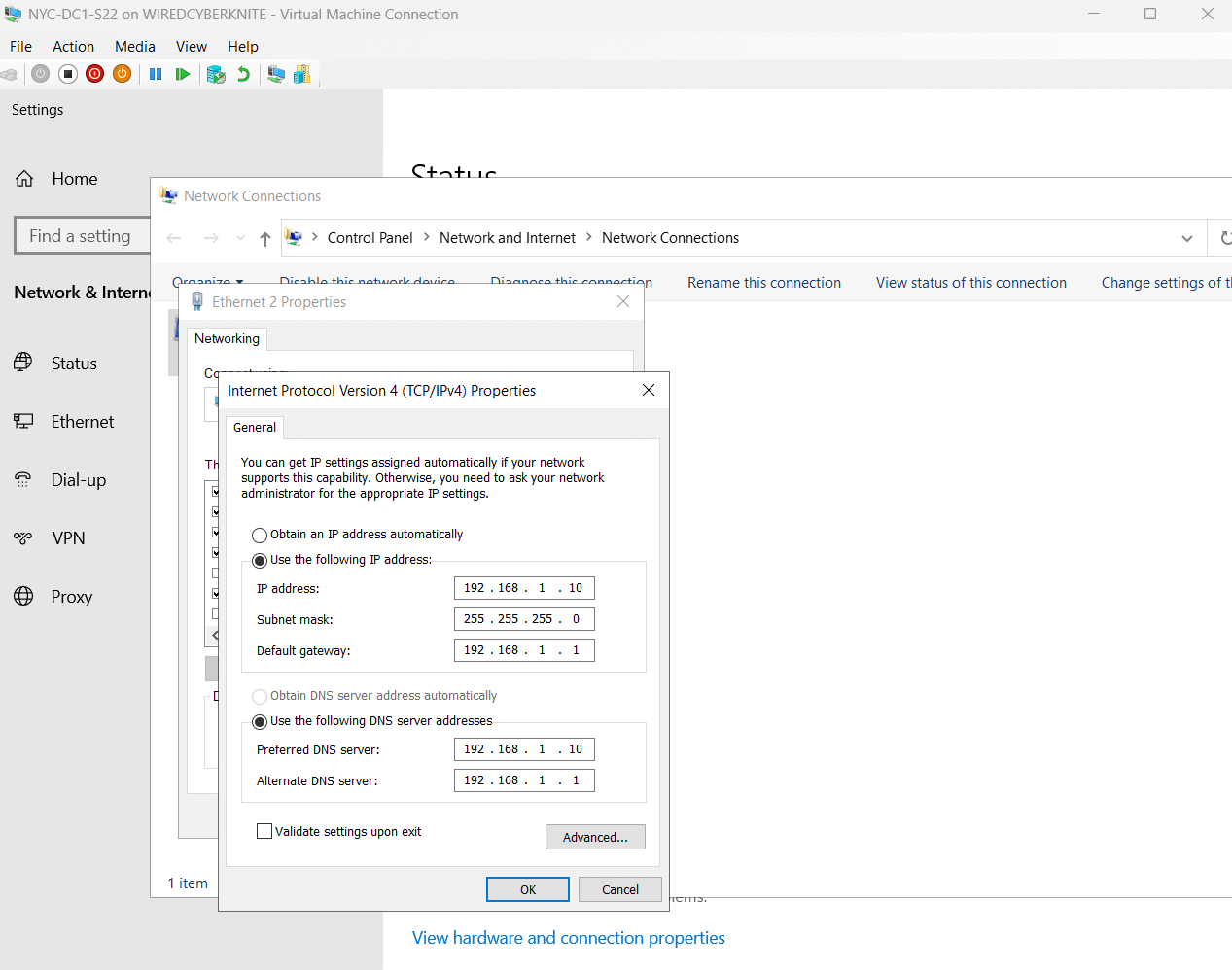
- Renamed the server to NYC-DC1-S22
- Assigned it a static IP of 192.168.1.10/24
I specifically avoided using .1 to leave that address available for pfSense, which I’ll install in Day 2 as my internal lab firewall/router.

Step 2: Configured the Windows 10 Client (NYC-CLI1-W10)
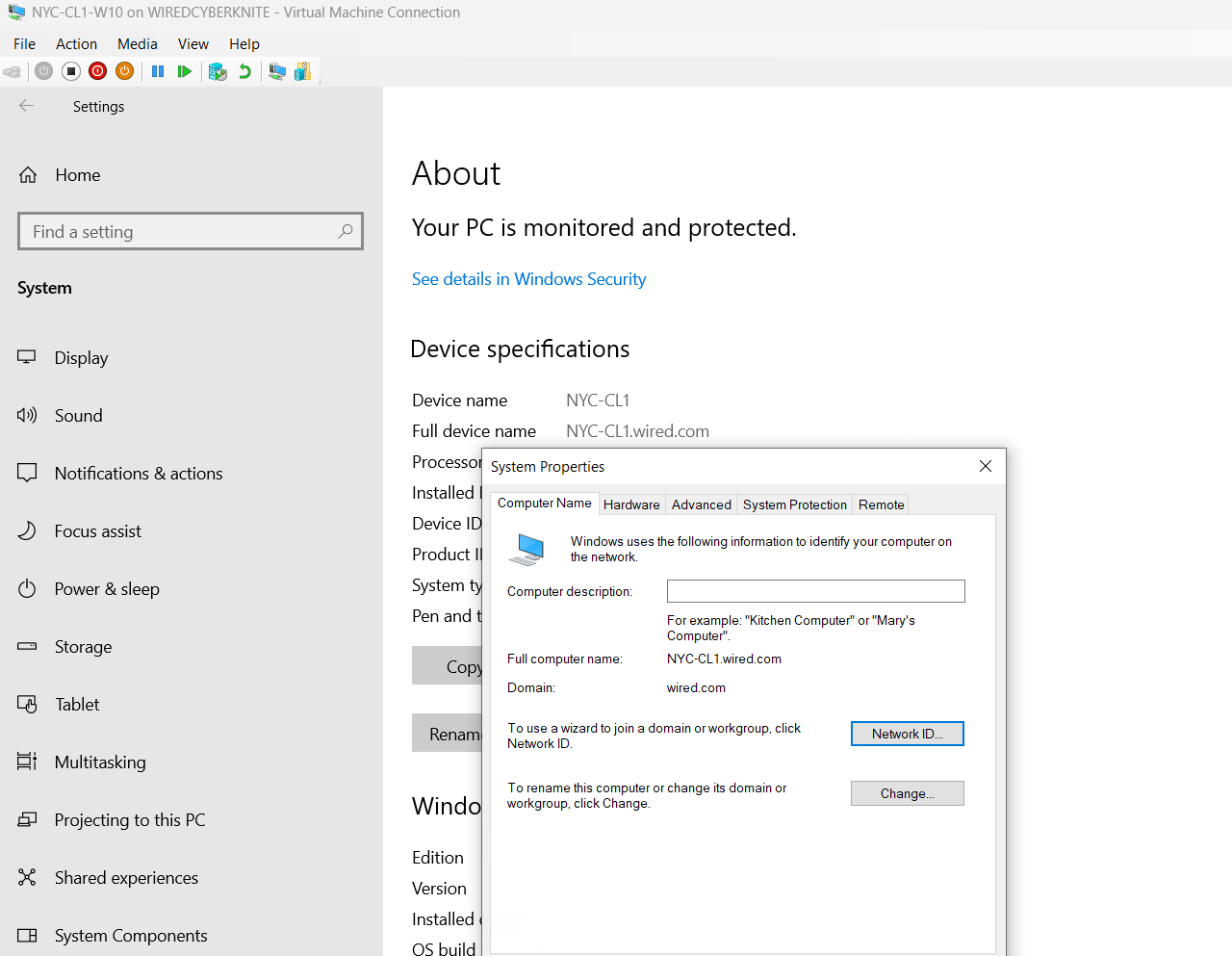
- Client name: NYC-CLI1-W10
- Left the IP to be assigned via DHCP for now
- Set its DNS server manually to 192.168.1.10 so it could find and communicate with the domain controller when I join it later.
Step 3: Promoted the Server to a Domain Controller
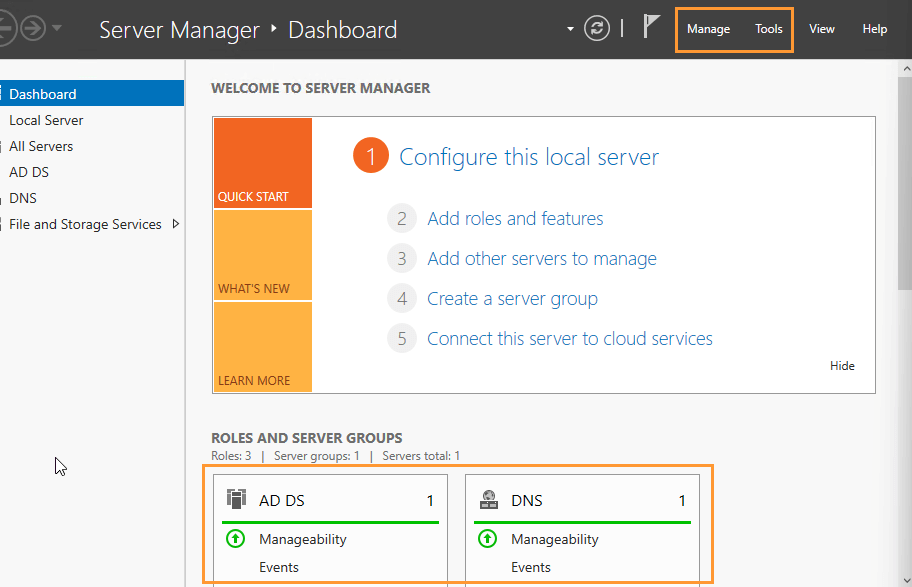
Using Server Manager, I installed the Active Directory Domain Services (AD DS) role, then used the built-in wizard to:
- Add a new forest
- Set the domain name to:
wired.com - Install DNS during the promotion process
- Set a DSRM password and complete configuration
After rebooting, the server came back fully promoted as a domain controller and DNS server — ready to manage my lab infrastructure.
Troubleshooting Tip
If you can’t ping your client from the DC or vice versa, make sure:
- The Windows Firewall is allowing ICMP (enable “File and Printer Sharing (Echo Request – ICMPv4-In)”)
- Both VMs are using the same internal virtual switch
- Subnet masks are set to 255.255.255.0 (for 192.168.1.x/24
What’s Next?
In Day 2, I’ll deploy pfSense to create a real firewall between VMs, simulate VLAN-like segmentation, and eventually control inter-VM traffic between VMware and Hyper-V.
This firewall will become the lab’s gateway and set the stage for connecting to cloud platforms like Microsoft Entra ID and Azure later in the series.
What I Learned
- How to configure a static IP and prepare for network segmentation
- How to deploy and promote a Windows Server as a domain controller
- The importance of DNS when joining client machines to a domain
- Why IP planning and gateway assignment matter before layering in a firewall like pfSense
Follow the Journey
This post is part of my Real-World IT Lab in 10 Day blog series.
Check out Day 2 where I’ll route all lab traffic through pfSense and build out the first step of my hybrid network design.
Follow me on LinkedIn for more behind-the-scenes insights and weekly updates!


Leave a Reply